Prefetch and Antiforensics on Windows 11
Notes
Originally written for a university artefact research project, I was limited in scope by a rubric and wordcount but still enjoyed the deep dive. Since this was written, some of the prefetch tools have been updated to identify 1F which is cool to see. It’s easy to pop a disk into autopsy and believe that the timeline generated is reliable, and certainly it uses more than prefetch, but if anything, this exercise reminded me to always verify - even what is appearing in forensics tools.
Summary
Prefetch is a Windows feature designed to improve performance that was first introduced in 2001 and is provided as part of the Sysmain service on current versions of Windows. Prefetch generates files that contain application execution metadata, and this metadata makes prefetch files a valuable forensic artefact. Windows 11 Insider Build 26100 introduces the undocumented prefetch Version 1F (Hexadecimal) or 31 (Decimal). Currently, none of the available tools for prefetch analysis, or research on prefetch, recognise this version (NOTE: Tools have since been updated to reflect this change).
The primary purpose of this research is to analyse both prefetch Version 31 and Version 30 on Windows 10 and 11, to identify changes and undocumented features as well as to determine if tried and true anti-forensics methods targeting prefetch are still effective. This analysis concluded the following: • Firstly, a comparative analysis of file paths accessed within prefetch files revealed a new forensic capability of prefetch in Windows 11: the ability to determine which specific language codepages were loaded by an application in the first ten seconds following execution. This is not specific to prefetch version 31 and is related to the way that Windows 11 handles codepages. • Secondly, Sysmain is undergoing notable improvements to efficiency, maintainability, and performance, but no new prefetch specific functionality was observed. Indeed, the only part of the file headers that has been altered is the version identifier. Prefetch analysis toolsets are currently unable to identify the version but have no issues extracting the data within. • Thirdly, five anti-forensics methods known to impact earlier versions of prefetch were still successful on Windows 11 Build 26100 / Prefetch version 31.
It is fitting that prefetch, which was never intended to be a forensic artefact, continues to gain additional, unintended forensic capability. It is reassuring to know that Sysmain and prefetch are being actively improved by Microsoft, and it is important to be aware that prefetch remains easily tampered with.
Prefetch Background
Prefetch was first introduced in 2001 with the purpose of increasing the speed of the boot process and the startup times of applications by “monitoring the data and code accessed by boot and application startups and using that information at the beginning of the subsequent boot or application startup” (Russinovich & Solomon, 2005). Put another way, prefetching loads data into memory before it is asked for, leveraging the significant disparity in access times between spinning disk hard drives and volatile memory to improve performance.
Prefetch files are metadata files containing information on the most recently executed applications. During the initial ten-seconds following process execution, the prefetch service actively monitors file references, such as loaded libraries and nested executions. These references are recorded as full paths within the prefetch file associated with a process, and this information is then cached into memory by the Sysmain service. Each process maintains a unique prefetch file, and modern systems are configured to store up to 1024 prefetch files.
Prefetch files are located within the %SystemRoot%\Prefetch directory. Each Prefetch file is named using a combination of the application’s name and an eight-character hexadecimal representation of a hash derived from the absolute path of the executable file. This means that if an executable with the same name is launched from a unique directory, it will have a distinctly calculated hash (Vouvoutsis, 2019). This also means that, for a given version of prefetch, system files with known directories have predictably named prefetch files, such as POWERSHELL.EXE-CA1AE517.pf.
Windows Vista introduced superfetch alongside prefetch, adding capabilities like behavioural analysis. Windows 10 Build 1809 combined prefetch and superfetch into the Sysmain service, which continues on Windows 11.
The effectiveness of the performance enhancement capabilities provided by prefetch is controversial, with widespread recommendations to disable prefetch on systems running solid state drives. Even Microsoft’s technical documentation once included instructions to disable superfetch on Windows 7 to protect solid state drive health, although this documentation has now been deleted and was only accessible through the internet archive (Microsoft, 2012).
The forensic value of prefetch was quickly established. In 2005, Gieger wrote about how prefetch can be used to determine the full path and names of files in wiped directories (Geiger, 2005). Prefetch files are now majorly used to determine the absolute path, execution datetime and number of executions of an executable, information well suited to creating forensic timelines.
Since 2005, the forensics community have invested significant effort in reverse engineering prefetch related binaries, and the development of tools to forensically process prefetch data. Much of the understanding of the internal structure and forensic value of prefetch files has been derived from this research, but there is a noticeable lack of information relevant to Windows 11, in large part due to the fact that the current release of Windows 11 still uses the same prefetch file format as Windows 10, identified by the first byte of the uncompressed file header – 1E, or 30 in decimal.
When examining prefetch on Windows 11 Insider Preview Build 26100, prefetch version 1F (V31) was observed. Significantly, no existing documentation or references to prefetch V31 could be found.
The technical analysis is limited in scope to the versions of Windows, Sysmain.dll, and Prefetch File version below:
Windows 10 Build 19045 | 10.0.19041.3803 | 1E (V30)
Windows 11 Build 22631 | 10.0.22621.3672 | 1E (V30)
Windows 11 Build 26100 | 10.0.26100.1150 | 1F (V31)
Version Identifiers
Prior to the introduction of Sysmain, prefetch files were uncompressed and were identifiable by their distinct file signature “SCCA”. Sysmain compresses prefetch files with the Microsoft XPRESS Huffman (LZXPRESS) algorithm, and compressed prefetch files have a file signature of “MAM” (Metz, 2023). The compressed file signature of prefetch V31 is unchanged from previous iterations.
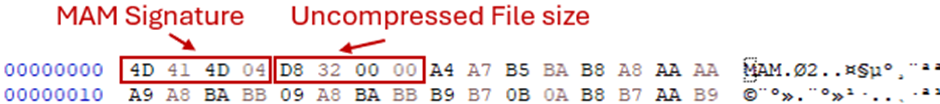
A recreation of the decompressed file header structure diagram created by Venault in Fooling Windows through Superfetch (Venault, 2020) shows that the header structure is identical, except for the version identifier 1F at offset 0x00000000.
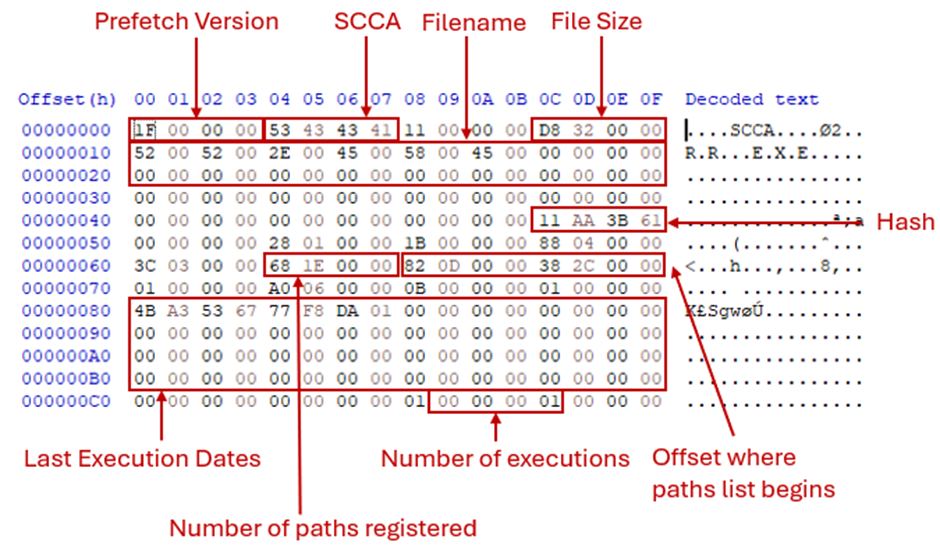
Metz indicates that this identifier is indicative of the Operating System version (Metz, 2023), however, earlier versions of Windows 11 continue to use the 1E format, so it is now more correct to say this is tied to the Prefetch File format version.
When compared to the prefetch file generated by prefetch V30, the number of paths accessed and hence the file size varied while the offsets remained statically located within the file header. Of note is the presence of specific codepages only on Windows 11.
Codepages
Prefetch’s interaction with codepages has been documented from the very beginning of Windows XP in 2001 (Russinovich & Solomon, 2001). The major, seemingly undocumented feature difference between Windows 10 and 11 is that specific language codepage files within the System32 directory are shown in prefetch files in both Windows 11 versions.
Most prefetch entries on the test systems showed exclusively C_1252.NLS (ANSI Latin 1; Western European) and C_437.NLS (OEM United States), with C_28591.NLS (ISO 8859-1 Latin 1; Western European) appearing less frequently. All codepage numbers in this section were identified through Microsoft documentation (Satran, Ye, Sharkey, & Bridge, 2021).
When opening files that contain other languages, even without installing language packs, new codepages could be seen in prefetch entries. Two documents were opened containing languages that used alternative codepages in Notepad.
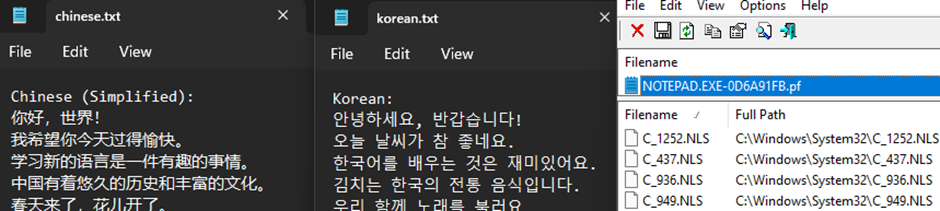
The two additional codepages match the loaded languages:
C_936.NLS (Simplified Chinese GBK)
C_949.NLS (Korean (Unified Hangul Code))
A Chinese ransomware sample (FUNNY.EXE - MD5 b44191b05ede23da1c048758cef2e87e) was executed and the prefetch entry contained C_936.NLS:
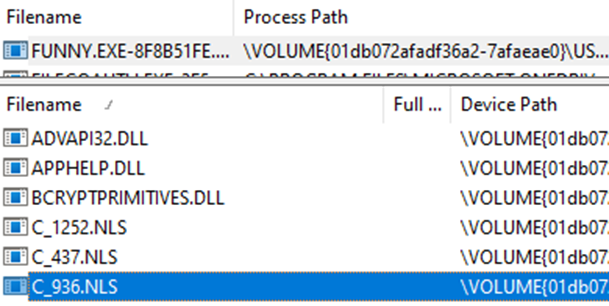
Other malware samples were observed interacting with the codepages C_936.NLS, C_949.NLS, C_932.NLS (Japanese) and C_950.NLS (Traditional Chinese) (Valkyrie, 2018).
Analysis with Procmon64 showed that the prefetch entries documented in Figures 4 and 5 were being accessed on both versions of Windows 11 by taskhostw.exe.
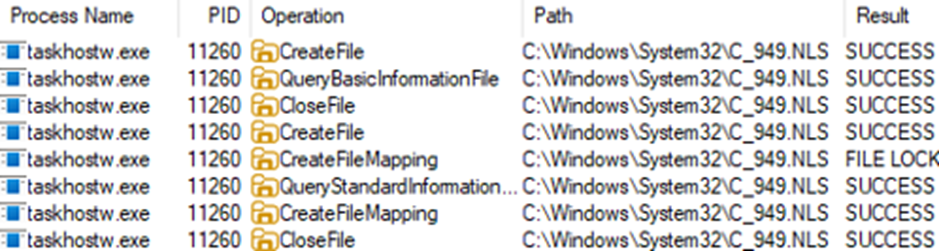
On Windows 10, a near identical operation sequence occurred with consent.exe instead of taskhostw.exe
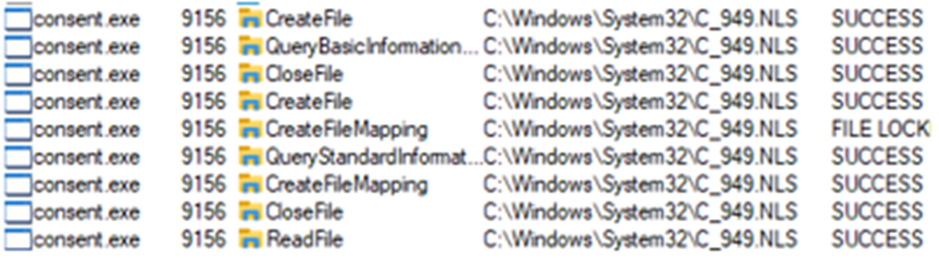
So without digging too deeply into API’s, it appears that this feature is due to a change in Windows operating system functionality that prefetch benefits from, but not a change to prefetch itself. It’s kind of cool that you can see this but the chances of it actually being forensically useful are slim.
Sysmain.dll Changes
This was confirmed by analysing the Sysmain.dll variants in IDA. This analysis found that each version in scope loaded the same functions to interact with NLS files: PfXPLocateNlsFile and PfXpQueryNlsFileName, and that these functions were identical across all versions with the exception of a renamed variable from Sr to Systemroot_0.
Windows 11 Build 26100’s Sysmain.dll included 66 prefetch specific functions that were not present in Windows 11 Build 22631. 46 prefetch specific functions had actually been removed and replaced between the two Windows 11 versions.
In fact so much changed between versions that doing a full comparison seemed a bit insane, but a closer look at a sample of the new functions shows that an effort appears to be being made to centralise imports. For example, when comparing the function PfSvRecreateDynamicPriorityDbs between versions, older versions of Sysmain.dll directly import GetSystemTimeAsFileTime from kernelbase.dll. The latest version calls the newly defined PfsGetSystemTimeinSeconds, which imports GetSystemTimeAsFileTime from kernelbase.dll (Figure 9). The functionality is essentially identical, but the maintainability of the code is enhanced, as updating one import instead of many is simpler and less prone to error.
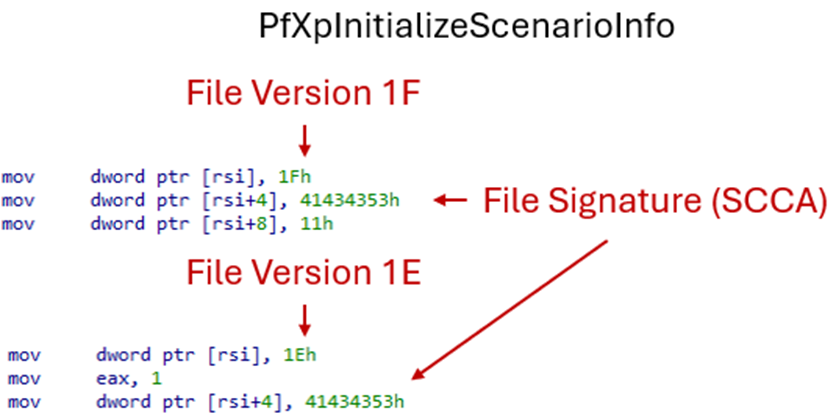
The new file version identifier 1F is hardcoded into the PfXpInitializeScenarioInfo function:
The other interesting change is that there is a noteicable trend towards using Single Instruction Multiple Data (SIMD) parallelism, with the addition of the xorps instruction to zero out SIMD registers efficiently, and additional uses of the movups instruction. On modern CPU’s, SIMD can mean anywhere from a two to sixteen-time performance optimisation (Parker, 2024).
| Instruction | Count on Sysmain 10.0.19041.3803 | Count on Sysmain 10.0.22621.3672 | Count on Sysmain 10.0.26100.1150 |
|---|---|---|---|
| movups | 1735 | 1743 | 2141 |
| xorps | 486 | 498 | 723 |
The interesting and likely unintended side effect of these modernisation efforts is that existing prefetch hooking and injection methods will cease to function.
The forensic implication of these modernisation efforts is that as endeavours continue, existing hooking and injection methods will cease to function. As demonstrated in DLL injection below, the PfSvWriteBufferEx function contains a direct import that has been exploited to develop a prefetch muter. This function remains unchanged in the current version of Sysmain.dll so prefetch is still mutable using legacy tools.
Registry
The registry keys of importance for prefetch are :
HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\Prefetch Parameters
HKLM\SYSTEM\CurrentControlSet\Services\Sysmain
Prefetch Parameters contains the EnablePrefetcher REG_DWORD which controls prefetch behaviour. The value can be adjusted to 1 for application prefetching only, 2 for boot prefetching only, 3 for both (the default setting), or 0 to disable prefetching. No changes to Prefetch Parameters were discovered on Windows 11 Build 26100.
The Sysmain key contains the service specific settings for Sysmain. The REG_MULTI_SZ value RequiredPrivileges was updated to include SeCreateGlobalPrivilege, which allows the creation of global file mapping and symbolic link objects (Pamnani, 2017). As services commonly have this permission (on my test system, 91 services did) this is unlikely to have any forensic or security implications.
The script used to analyse these service permissions is below. It could probably be more efficient but it works well.
$result = Get-ChildItem -Path "HKLM:\SYSTEM\CurrentControlSet\Services" |
Where-Object { $_.PSIsContainer } |
ForEach-Object {
$requiredPrivileges = $_.GetValue('RequiredPrivileges')
if ($null -ne $requiredPrivileges) {
$privileges = $requiredPrivileges -split '\r\n'
if ($privileges -contains 'SeCreateGlobalPrivilege') {
[PSCustomObject]@{
Service = $_.PSChildName
RequiredPrivileges = $privileges -join ', '
}
}
}
}
$count = $result | Measure-Object | Select-Object -ExpandProperty Count
Write-Host "Number of services with SeCreateGlobalPrivilege: $count"
Write-Host ""
$result | Format-Table -AutoSize
Prefetch Anti-Forensics
Just delete them bro
I used a powershell script to confirm if “just delete them” still works the same way as older OS’s. The sleep for 11 seconds was to ensure that prefetch actually made a file because even though it’s supposed to be 10 seconds, it seems very inconsistent in practice.
$notepad = Start-Process notepad -PassThru
$notepadStartTime = $notepad.StartTime
sleep -Seconds 11
$powershell = start-process powershell "Write-Host test" -PassThru
$powershellStartTime = $powershell.StartTime
sleep -Seconds 11
$pspffn = get-item C:\windows\Prefetch\powershell.exe*.pf
Remove-Item -path $pspffn.FullName -Force
$calc = start-process calc -PassThru
$calcStartTime = $calc.StartTime
Write-Host "Summary:"
Write-Host "Notepad started at: $notepadStartTime"
Write-Host "PowerShell started at: $powershellStartTime"
Write-Host "Calculator started at: $calcStartTime"
Running the script:
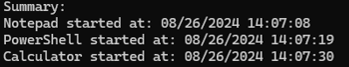
WinPrefetchView shows NOTEPAD.EXE, CALC.EXE, and PING.EXE. POWERSHELL.EXE is missing as expected. Execution times are consistent with the script. The presence of CONHOST.EXE also indicates that PowerShell was launched.
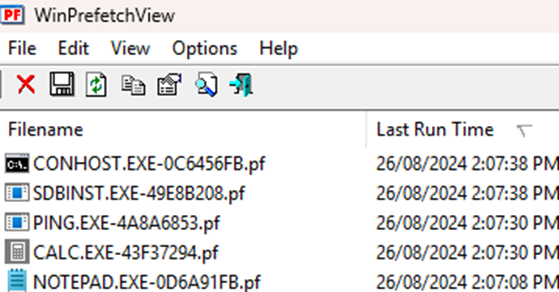
These file deletion activities are easily detectable in UsnJrnl / $J of course

Prefetch file hex-editing
As shown above, the execution timestamp is stored in the header at offset 0x00000080 and this hasn’t changed which means that the tool written by Venault in 2020 still works to modify prefetch however you like. Note that this prefetch file was copied from another system which is why the process path is a GUID. It really seems like a lot of effort for little gain to modify prefetch files like this, but it’s still cool that it works.
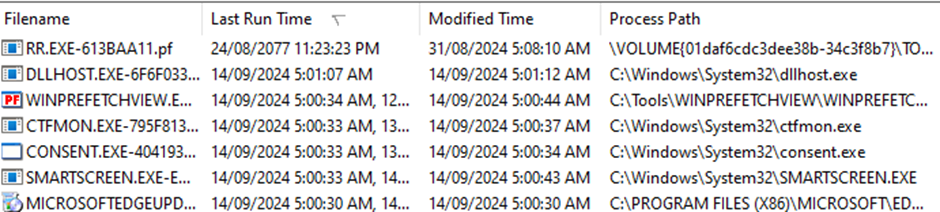
Killing Sysmain Service
Finding the Sysmain service and stopping it prevents further events from being created temporarily, but as soon as the prefetch service is restarted, these entries can reappear. Setting the Sysmain service to disable automatic restarting can bypass this, and rebooting the system before restarting also still prevents these prefetch entries from being created. This seems like a much more elegant way to bypass prefetch recording - simply kill the service, run your evil, and then reboot.
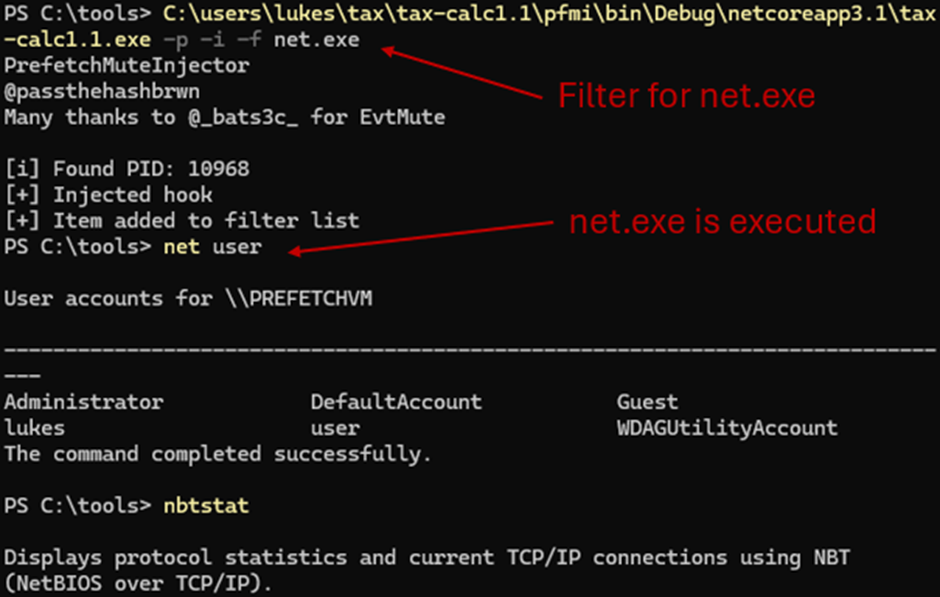
DLL Injection
As mentioned above, DLL Injections using PrefetchMuteInjector by @Passthehashbrwn looked like it should still work based on the functions remaining unchanged.
Alternate Data Streams
Metz (Metz, 2023) and Vouvoutsis (Vouvoutsis, 2019) state that using Alternate Data Streams creates a prefetch file named for the alternate data stream. However, this was easily bypassed on all versions of Windows with the below method.
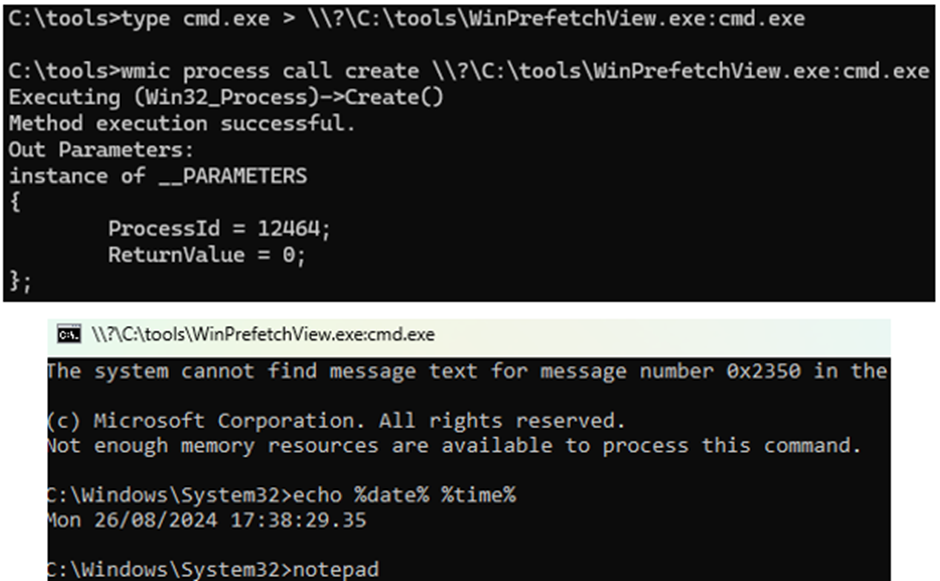
However doing so is very noisy regardless because of WMI:
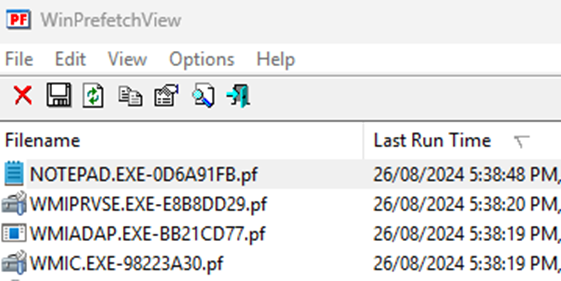
Conclusions
Prefetch files remain vulnerable to tampering efforts of varying complexity. The information contained is limited to a snapshot with 10 seconds worth of activity, and additional metadata inside prefetch files that can show nested execution is inconsistently overwritten. It is vital to contextualise these forensic limitations by understanding that prefetch was never primarily designed or intended as an immutable source of forensic evidence.
The presence and content of a prefetch file alone is not a definitive source of evidence that can be relied upon beyond reasonable doubt. However, when used as a tool for correlation, prefetch is a potent source of metadata that can increase the reliability of other sources of evidence. Indeed, even the lack of prefetch files, or evidence of prefetch tampering, are both valuable indicators of compromise.
The scope of this analysis was constrained by a limited laboratory environment utilising only three Windows versions. A more comprehensive investigation would require a broader range of Windows versions to account for the significant variations observed in Sysmain.dll, even within the same Windows release.
Furthermore, the comparative analysis of disassembled functions did not examine every single function, and a representative sample was selected for analysis. A more exhaustive examination is necessary to fully understand any new or removed features in Sysmain.dll, and to document predicted import centralisation efforts.
References
Geiger, M. (2005). Evaluating Commercial Counter-Forensic Tools. Paper presented at the DFRWS.
Metz, J. (2023). Windows Prefetch File (PF) format. Retrieved from https://github.com/libyal/libscca/blob/main/documentation/Windows%20Prefetch%20File%20(PF)%20format.asciidoc
Microsoft. (2012). Windows 7 & SSD: defragmentation, SuperFetch, prefetch. Retrieved from https://web.archive.org/web/20130219063512/http://support.microsoft.com/kb/2727880
Oh, J., Lee, S., & Hwang, H. (2024). Forensic Detection of Timestamp Manipulation for Digital Forensic Investigation. IEEE Access.
Pamnani, V. (2017). Create global objects. Retrieved from https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/security-policy-settings/create-global-objects
Parker, C. (2024). SIMD: A practical guide. Retrieved from https://lowleveldev.substack.com/p/simd-a-practical-guide
passthehashbrowns. (2020). PrefetchMute. Retrieved from https://github.com/passthehashbrowns/PrefetchMute
Russinovich, M. E., & Solomon, D. A. (2001). Windows XP: Kernel Improvements Create a More Robust, Powerful, and Scalable OS. Retrieved from https://learn.microsoft.com/en-us/archive/msdn-magazine/2001/december/windows-xp-kernel-improvements-create-a-more-robust-powerful-and-scalable-os
Russinovich, M. E., & Solomon, D. A. (2005). Microsoft Windows Internals: Microsoft Windows Server 2003, Windows XP, and Windows 2000: Microsoft Press.
Satran, M., Ye, C., Sharkey, K., & Bridge, K. (2021). Code Pages Identifiers. Retrieved from https://learn.microsoft.com/en-us/windows/win32/intl/code-page-identifiers
Valkyrie. (2018). Malware Analysis Report on f57808e1d32549fd59e33d8dc2646157cab0c536. Retrieved from https://valkyrie.comodo.com/kill/chain/f57808e1d32549fd59e33d8dc2646157cab0c536/pdf/report/export
Venault, M. D., Baptiste. (2020). Fooling Windows through Superfetch. Retrieved from https://i.blackhat.com/USA-20/Thursday/us-20-Venault-Fooling-Windows-Through-Superfetch.pdf
Vouvoutsis, V. (2019). Manipulating and generating Windows 10 Prefetch files. Πανεπιστήμιο Πειραιώς,